|
The System
| |
|
Computer
| |
|
Function
|
Coordinates maintenance and defense network inside the submachines
|
The System is the binary coded program of Submachine. It provides information for the submachines and the sub-bots that maintain it and supports the artificial intelligence S.H.I.V.A..
History[]
The system was first featured in Submachine 6: The Edge when the player was exploring the defense system (DS). The player was sent by Murtaugh to "Explore the defenses and return unharmed" which at first seemed to be a peaceful operation. When the mover from Submachine 5: The Root was intercepted by the DS, it became evident after reading a message from Murtaugh that the player had no choice but to disable the primary defense system, found in the mainframe. This resulted in the defense systems going completely offline and leaving the Core unprotected from a possible invasion by Murtaugh's forces. After the mainframe was taken offline, the player received a message from Murtaugh followed by a complete shutdown, leaving the player trapped. Murtaugh's message ends with: "The adventure is now over for you. Goodbye." From the beginning, Murtaugh had known that he would have to sacrifice, with good or bad intent, the player. The player was "not the first, and certainly not the last" one sent there.
There is sufficient proof that the entire journey of the player in Submachines 5 and 6, guided by Murtaugh, maybe have been the results of following automatic protocols set by Murtaugh even after his goals had been achieved.
System components[]
The System mainly consists of:
- Terminals
- Gates
- Switches
- Connections
- Graphs
- Protocols
- Alerts
- Main article: Terminal
The player is able to interact with the system by connecting a connection pod with one of the numerous terminals within the Subnet Defense System. Terminals serve as access points to the System. They are circular receptacles into which connection pods may be inserted.
As far as is known, each terminal connects to an individual section of the System. Some sections are, however, virtually interconnected (via a gate and switch pair).
The original purpose of the terminals was for maintenance purposes by sub-bots.
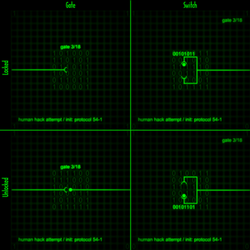
Example of a gate-and-switch pair.
A gate is a point along the connection in a terminal which when open, allows someone to proceed further into a program. When closed, it prevents them from going any further.
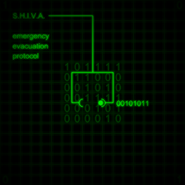
A gate can be controlled via its corresponding switch. Switches can be anywhere in the same terminal or in another. When locked, a switch reads "00101011" (+). When unlocked, it reads "00101101" (-).
Gates that have been found so far include:
- Gate 1-0: Protects the mainframe protocol, 1-0.
- Gate 1-12: Protects the primary defense system. Is unlocked by disabling protocols 1-28, 1-32 and 1-35. It may also require the disabling of the secondary defense system (protocol 2-18).
- Gate 3/18: Protects protocol series 54-n. Located in the first terminal in Area 8 and is opened by the second terminal in the same area.
- Gate 115: Found within the mainframe terminal. Protects a switch that partially unlocks the connection to the 1-n protocol series.
Connections are green paths that connect a gate to a protocol/set of protocols, or to another gate/switch pair.
A graph in the System is generally a large visual infographic or control system. Currently known graphs include:
- Elevator: Found in the second terminal of Area 8. Protected by protocol 54-3. Controls the Area 8 elevator.
- Personal Identification Number (pIDN): Housed in Area 5. Presumably controls the pIDN system.
- Ventilation: Found in the first terminal of Area 8. Controls/displays a set of six fans.
- Subnet Infestation Map: Found in the Area 4 terminal. Protected by protocol 54-4. Displays human infestation of subnet.
- Security Level Control Panel: Found in Area 4. Controls the electrical barrier on level 1.
- Informational Graphs: Panels showing info about the subnet or even essays of Subnet theorists (Example: Edge as Boundary Theory by Robobrain in 757).
A protocol of the System is a function thereof. Protocols may be enabled or disabled.
Protocols are numbered n-n, where n is a positive integer (Example: 1-12).
Known protocols[]
- 1-n Series (Mainframe + Primary Defense System)
- 1-0: Mainframe
- 1-12: Primary Defense System
- 1-28: 1-12 Gate
- 1-32: 1-12 Gate
- 1-35: 1-12 Gate
- 2-n Series (Secondary Defense System)
- 2-17: Turret Chain Stabilization
- 2-18: Secondary Defense System + Turret Chain Reset
- 54-n Series (Human Hack Prevention)
- 54-1: Start Other 54-n Protocols
- 54-2: Defense System Firewall
- 54-3: Hide Elevator Graph
- 54-4: Hide Subnet Infestation Map
If a protocol is locked to a position, the following message will be displayed:
- 01101100011011110
- 11000110110101101
- 10010101100100000
- 0110100001010
This translates from binary to text as "locked".
Unknown protocols[]
Other protocols that have been mentioned include:
- A protocol that tracks and imprisons/quarantines human infiltrators.
- A protocol that ejects connection pods in case the System or a specific terminal which the connection pod is plugged into shuts down.
- A protocol that fully shuts down the S.H.I.V.A. supercomputer in the event of an emergency.
It is probable that all functions of the Subnet are ultimately controlled by the System.
Systems have alerts for situations that are dangerous to it. The alerts for the subnet's system have three numbers in them in form #-#-#.
It seems that the Subnet regularly checks for alerts. For this there is a program of its own. It has a 5x5 grid of numbers. The numbers change as the scan continues. The numbers go from 0 to 9. If an alert factor is noticed, the number turns white and doesn't change anymore. Five numbers activate in the grid before the activation of an alert.
Only one alert is known by name (0-23-17).
This refers to the mover sequence between Sub5 and Sub6. The mover is then intercepted by the system, and the mover of section one was returned to its place as the player was taken to the edge.System functions[]
The system's overarching function is to provide power to and protect the subnet, which serves as the body for the artificial intelligence S.H.I.V.A.. It does this with a variety of components.
Defense system[]
This massive system of protocols houses:
- A primary defense system that contains a human recognition pattern in order to calibrate the secondary DS.
- A secondary defense system which controls a system of turrets to target and to remove humans from the subnet.
Elevators[]
Elevators are controlled by/in the System through the elevator graphs, with which the player can simply select the elevator icon (a square) which will change its place until it is in the desired position.
Movers[]
Movers are controlled by the System and seem to have some kind of a schedule to move on. They are used by the sub-bots, as a mean of transport.
If a mover were to move un-accordingly it will be intercepted by the System and be returned to its place, after the user has stepped onto a transport vehicle.
Portals[]
The system utilizes a network of edge portals to transport sub-bots. These edge portals became the basis for the reverse-engineered lab portals for use by humans. They are used by activating a system switch via a connection pod in a terminal in the front of the portal.
Sub-bots[]
Sub-bots work as maintenance units to the system and the subnet as a whole. They can work independently, but they confirm all their actions by sending messages to the system.
Maps[]
Trivia[]
- The design of the system reappears in Escape from Jayisgames (as well the ambient and sound effects).